Why technology isn't the weakest link in your cyber security strategy

This blog has been expertly reviewed by Darren Hogan, Director of Portfolio at Nasstar.
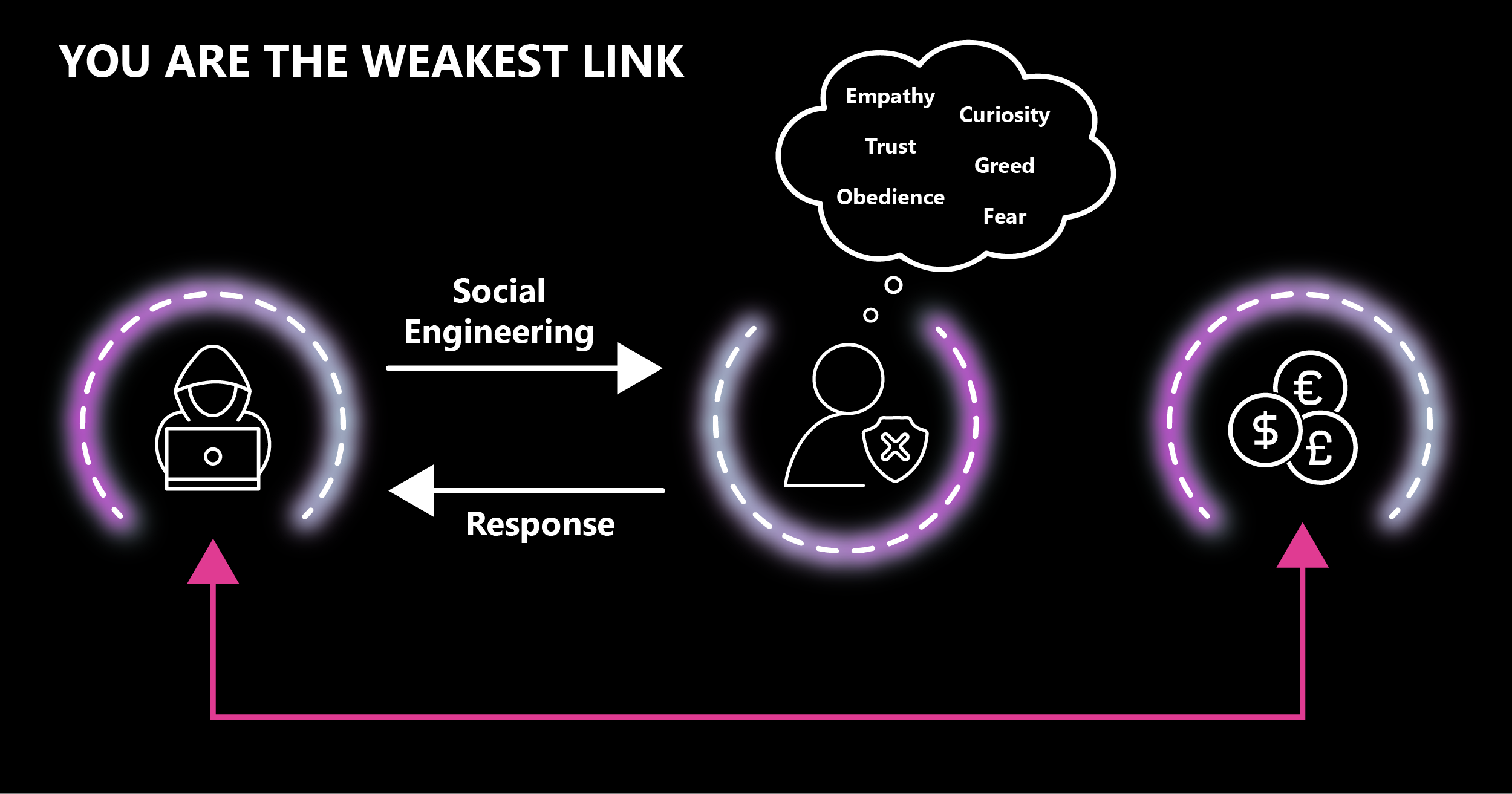
Threat actors are exploiting the human condition. Fear, empathy, and trust have become targets for the modern cyber-criminal, with phishing and other social engineering methods becoming standard. This means that when it comes to defending against cybercrime, the weakest link is... your people.
According to Gartner, lack of talent or human failure will be responsible for over half of significant cyber incidents by 2025. And to add to the problem, IBM’s 2023 Cost of a Data Breach Report found that breaches using stolen or compromised credentials took the longest to resolve, at 88 days (in a 328-day data breach lifecycle).
But how do you mitigate that risk and protect your data in the age of public cloud and remote work?
Unfortunately, the old “castle and moat” approach to IT infrastructure security is no longer good enough. Applications and services have migrated to public cloud, and users are accessing data from various locations. Likewise, traditional VPNs (virtual private networks) are flawed, allowing access to a range of applications at the network layer, rather than specific apps based on policy and additional security measures.
This is why a Zero Trust approach is required.
What is Zero Trust?
While you’ve likely heard of Zero Trust before, there are a few variations when it comes to defining and discussing it in practice. At its core, Zero Trust is a strategic model in cybersecurity that has been designed to protect digital business environments. This protection includes private and public clouds, SaaS applications, DevOps, and robotic process automation (RPA).
Initially becoming a buzzword for tech enthusiasts, Zero Trust has evolved into a business-critical framework for adoption in every organisation. It works on the premise that you cannot always distinguish the good from the bad, so never trust and always verify. Every user must be authorised, verified, and encrypted in real time before resource access is granted.
You may already have identity-based Zero Trust solutions in your organisation like single sign-on (SSO) and multi-factor authentication (MFA). These systems work to ensure that only individuals, devices, and apps can access a business’ systems and data.
The human factor
Humans are driven by emotions that can be readily exploited by cyber criminals. This is important when considering a Zero Trust approach to cybersecurity. Darren Hogan, Director of Portfolio at Nasstar provides the following examples:
“Let’s first take obedience/fear. Say an employee in the finance department receives a text message from their “CEO” instructing them to send a payment to a third party for a service received as part of the ongoing refinancing of the business. This needs to be done within the next 30 minutes otherwise the company will not meet the deadlines for refinancing.
“The employee does as they are told. This means the threat actor has successfully extorted funds without ever having to deploy any kind of ransomware. This is the simplest and cleanest form of cybercrime.
“To combat this, the adoption of a Zero Trust architecture and mindset is needed to complement the technology solution. A policy of communications from senior leadership team members to staff only through trusted and verified methods (not text messages) would be an appropriate starting point.
“Another human example is curiosity. Imagine an employee has received an email in error from HR with a spreadsheet attachment titled ‘Company Bonus Scheme Draft’. Natural curiosity takes over and the employee opens the attachment.
“The attachment launches a virus that encrypts all files on the user’s machine and travels laterally to other users. The organisation is then at the mercy of the cybercriminal via a ransomware attack.
“Again, training and the Zero Trust mindset come into play. Refusing temptation and reporting the incident would help limit the blast radius. In conjunction, modern unified threat management (UTM) technologies such as sandboxing can help to isolate suspicious email attachments, executing them in a safe digital location to observe and document their behaviour before flagging and removing similar attachments in the future.”
Companies must assume people will continue to be the largest point of failure in today’s cybersecurity posture systems.
Organisations must also assume that they’ll continue to be susceptible to social engineering, presuming a breach will happen at some point. Businesses should therefore strongly consider exploring a Zero Trust approach.
Zero Trust at Nasstar
Security is always front of mind for us, and we apply the same thought process to the businesses of our customers. As such, our Microsoft SSE offerings (Entra Internet Access and Entra Private Access) have been created as an addition to our existing Intelligent Connected Cloud (ICC) connectivity portfolio – ICC Access, SD-WAN, and ICC Cloud Connect.
Entra Internet Access is a cloud based Secure Web Gateway (SWG) solution for Internet-based SaaS apps and Microsoft 365 apps. It uses a policy engine to allow or deny traffic based on the principles of Zero Trust.
With Entra Private Access, private applications are protected via the concept of an application proxy. The proxy server sits in the private application environment and brokers connections to private applications based on the credentials of the user and the policy delivered by Entra ID. This forms a credible alternative to legacy VPNs by providing secure “per-app” access to applications.
Each of these new Microsoft offerings delivers on the principles of a Zero Trust Network Access (ZTNA) solution, constantly verifying the identity, context, and policy adherence of users before allowing access to critical business resources and data.
Embedding ZTNA in a modern integrated cloud and connectivity solution allows customers to build a defence-in-depth approach to security posture management. Building guardrails around users and data with ZTNA, then expanding beyond the user’s span of control to incorporate devices with branch-level security controls (such as unified threat protection) can significantly reduce the attack surface available to threat actors.
If you’re in the middle of a digital transformation journey, ZTNA can complement your existing tech stack and bolster the security of your users and data. Whether you’re reviewing cloud adoption strategies, actively migrating to a public cloud solution or firmly in the cloud and thriving, ZTNA is the ideal wraparound for security.
Embedding Zero Trust in your organisation
Organisations cannot afford to ignore the Zero Trust approach in favour of outdated and insecure frameworks. Keeping user, business, and customer data secure is more important than ever.
The global average cost of a data breach in 2023 was £3.5 million. That’s a 15% increase over three years. Is that really a cost you can afford to absorb?
Security controls need to exist in every aspect of technology, from connectivity to cloud and everything in between. Implementing the principles of Zero Trust into modern integrated infrastructure is a key enabler for a robust security posture.
Rebuild your security defences by booking a meeting to discuss ZTNA with a Nasstar expert today.



